I know the Seth Rich murder has been covered ad naseum. So I’m gonna make this brief and to the point.
I just wanted to point out a couple things that I saw reported back when it happened that I havent heard a word about since.
In August of 2016 I was browsing through a 4chan forum and I took this screenshot of a conversation (screenshot below) where Anonymous was claiming that they had hacked into Huma Abedin’s personal computer and had intercepted Huma in real time, sending the Saudis a compromising video that she had taken of Hillary. It is not stated what exactly was on the video but my guess is that it probably had something to do with the sexual abuse of a minor.
(Apparently Angela Merkel was also in one of the “compromising videos” with Hillary. God only knows what it shows them doing.)
Huma Abedin’s family is in Saudi Arabia and this is where her loyalty lies.
Anonymous confronted Huma and faced with the threat of being exposed, she agreed to give them info (the emails that were later printed by Wikileaks) if they agreed to keep quiet about what they found her doing.
According to Anonymous, Huma told them that she would give them the info they’d asked for via an insider…a liasion.
Guess who that liasion was? SETH RICH!!
Now does it make sense why they are trying to confuse this story?
HUMA WAS THE LEAK!!
Anonymous then gave the emails to Wikileaks to publish.
Here is that screenshot from 4chan. This was big news back then in forums like 4Chan and GLP…but it never seemed to reach any of the mainstream alternative sites and it seems to have been forgotten about since…




Source: Seth Rich Was Huma Abedin’s Liasion to Leak Clinton Emails After She Was Blackmailed by Anonymous. Huma was the leak! | Alternative








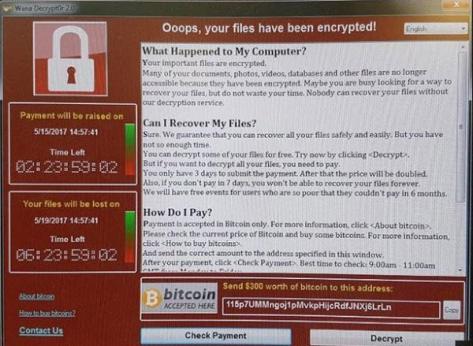
 A few days ago we discussed the fact that the New Computer Virus taking control of Banks and failing Hospitals was released by Microsoft and the “CURE” for the virus was created even before the Virus was released – forcing you to update into “Windows 11” and their “Smart Cloud.”
A few days ago we discussed the fact that the New Computer Virus taking control of Banks and failing Hospitals was released by Microsoft and the “CURE” for the virus was created even before the Virus was released – forcing you to update into “Windows 11” and their “Smart Cloud.”